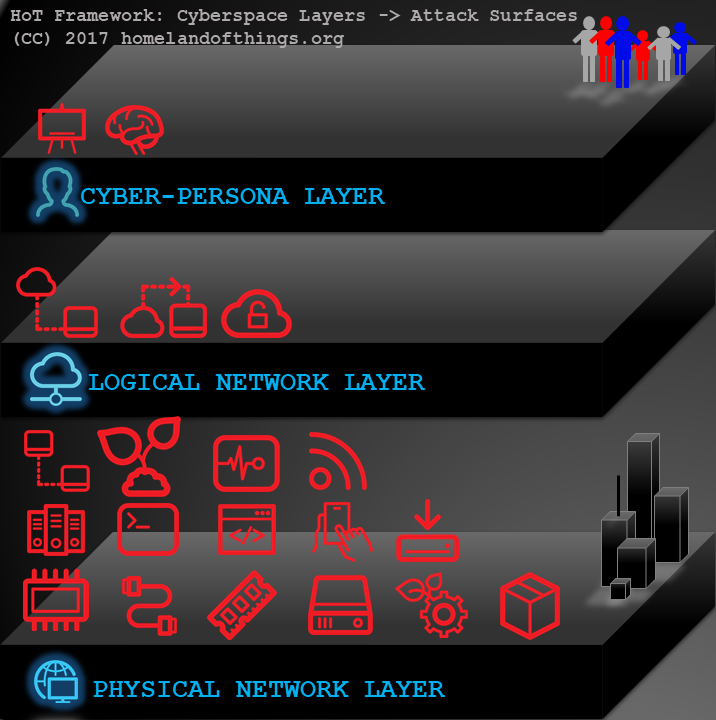
Cyberspace Layers -> Attack Surfaces -> TAIs
/// BLUF: Each of the HoT Framework's target areas of interest (TAI) consist of vulnerability summaries / definitions, a risk assessment (technical impacts, detectability, prevalence, and exploitability), attack surface and cyberspace layer mappings, known intrusion / exploit / attack cases and threats, mapped CVEs, tools and training for identifying and protecting vulnerabilities associated with the TAI, and tools and training for detecting, responding, and recovering from intrusions / attacks against the TAI. ///
- CURRENT TOTAL TAIs: 39
- CURRENT TOTAL ATTACK SURFACES: 19
This section connects the dots between the cyberspace layers (JP 3-12), the IoT attack surfaces (OWASP IoT Project), and HoT "Targeted Areas of Interest (TAI).
According to Army FM 3-90-1, in traditional offensive and defensive kinetic warfare, a TAI is:
"the geographical area or point along a mobility corridor where successful interdiction will cause the enemy to abandon a particular course of action or require the enemy to use specialized engineer support to continue. It is where the enemy force can be acquired and engaged by friendly forces."
The DoD Dictionary of Military and Associated Terms defines a mobility corridor as:
"an area where a military force will be canalized (channeled) due to terrain restrictions. It allows forces to capitalize on the principles of mass and speed, and needs to be relatively free of obstacles."
The old FM 71-123 Command, Control, and Communication adds that:
"mobility corridors can be combined to make avenues of approach"
Essentially, each asset/device can be considered a mobility corridor as each asset/device can be exploited and utilized for subsequent lateral movement. Each type of IoT vulnerability is considered a "target area of interest" as it is a point within a asset/device through which an threat actor's lateral movement depends upon and a point at which a friendly force can interdict. Each TAI can exist across multiple attack surfaces.
For example, HoT-TAI-0001 describes "password / credential management". If friendly forces were to identify and mitigate/protect the vulnerabilities associated with this HoT-TAI (e.g. changing default credentials), they would successfully interdict a threat actor from moving forward with a COA that relies upon the vulnerability associated with this HoT-TAI. It is important, however, that the friendly force ensure that they have identified, mitigated/protected, and have deployed attack detection capabilities for the vulnerabilities associated with the HoT-TAI at each of the asset's/device's attack surfaces, within each layer of cyberspace. In the event that friendly forces detect a threat actor attempting to out-maneuver friendly forces at the HoT-TAI, friendly forces will then utilize response and recover tools and training outlined in each HoT-TAI to ensure that the threat actor is contained and eradicated.
It is understood that capabilities and resources differ across organizations and individuals. Fortunately, the HoT Framework enables entities to select the HoT-TAIs that are within their capabilities and resources. It is totally up to you on how you assemble each of the HoT-TAIs to create your approach.
 Supply Chain
Supply Chain
- HoT-TAI-XXXX: Sourcing components from untrusted sources
- HoT-TAI-0024: Lack of tamper resistance
 Device Firmware
Device Firmware
- HoT-TAI-0001: Password / Credential Management
- HoT-TAI-0003: Buffer Overflow
- HoT-TAI-0005: Insecure 3rd party components / Vulnerable services
- HoT-TAI-0007: Weak access controls
- HoT-TAI-0014: Privilege Escalation
- HoT-TAI-0016: Security related function API exposure
- HoT-TAI-0031: Firmware downgrade possibility
- HoT-TAI-0032: No firmware version display and/or last update date
 Device Physical Interfaces
Device Physical Interfaces
- HoT-TAI-0014: Privilege escalation
- HoT-TAI-0023: Reset to insecure state
- HoT-TAI-0024: Lack of tamper resistance
- HoT-TAI-0025: Debug ports: UART (Serial) and JTAG / SWD
- HoT-TAI-0027: Removal of storage media
- HoT-TAI-0030: Firmware extraction
 Device EMS/RF/Wireless Interfaces
Device EMS/RF/Wireless Interfaces
- HoT-TAI-XXXX: TBD
 Device Memory
Device Memory
- HoT-TAI-0020: Cleartext storage of sensitive information in memory
 Local Data Storage
Local Data Storage
- HoT-TAI-0010: Weak or no data at rest encryption
- HoT-TAI-0039: Lack of data integrity checks
 Sensors
Sensors
- HoT-TAI-0024: Lack of tamper resistance
- HoT-TAI-0028: Sensing Environment Manipulation
 Network Traffic
Network Traffic
- HoT-TAI-0017: Protocol fuzzing
- HoT-TAI-0018: Non-standard Network Protocols
 Device Network Services
Device Network Services
- HoT-TAI-0001: Password / Credential Management
- HoT-TAI-0002: Injection
- HoT-TAI-0003: Buffer Overflow
- HoT-TAI-0004: Denial of Service (DoS)
- HoT-TAI-0005: Insecure 3rd party components / Vulnerable services
- HoT-TAI-0007: Weak access controls
- HoT-TAI-0008: Weak or no transport encryption
- HoT-TAI-0009: Weak or no authentication
- HoT-TAI-0013: Account lockout
- HoT-TAI-0014: Privilege Escalation
- HoT-TAI-0015: Replay attack
- HoT-TAI-0019: Insecure password recovery mechanism
- HoT-TAI-0022: Logging Options
- HoT-TAI-0029: Device Firmware OTA update blocked
 Administrative Interface
Administrative Interface
- HoT-TAI-0001: Password / Credential Management
- HoT-TAI-0007: Weak access controls
- HoT-TAI-0008: Weak or no transport encryption
- HoT-TAI-0009: Weak or no authentication
- HoT-TAI-0012: Insecure direct object references
- HoT-TAI-0013: Account lockout
- HoT-TAI-0014: Privilege Escalation
- HoT-TAI-0019: Insecure password recovery mechanism
- HoT-TAI-0022: Logging Options
- HoT-TAI-0038: Inability to wipe device
 Device Web Interface
Device Web Interface
- HoT-TAI-0001: Password / Credential Management
- HoT-TAI-0002: Injection
- HoT-TAI-0003: Buffer Overflow
- HoT-TAI-0007: Weak access controls
- HoT-TAI-0008: Weak or no transport encryption
- HoT-TAI-0009: Weak or no authentication
- HoT-TAI-0012: Insecure direct object references
- HoT-TAI-0013: Account lockout
- HoT-TAI-0014: Privilege Escalation
- HoT-TAI-0015: Replay attack
- HoT-TAI-0019: Insecure password recovery mechanism
- HoT-TAI-0022: Logging Options
 Ecosystem Communications
Ecosystem Communications
- HoT-TAI-0008: Weak or no transport encryption
- HoT-TAI-0009: Weak or no authentication
- HoT-TAI-0035: Inherently trusted ecosystem commands and updates
- HoT-TAI-0036: Insecure health checks
- HoT-TAI-0037: Insecure heartbeats
 Mobile Application
Mobile Application
- HoT-TAI-0001: Password / Credential Management
- HoT-TAI-0003: Buffer Overflow
- HoT-TAI-0007: Weak access controls
- HoT-TAI-0008: Weak or no transport encryption
- HoT-TAI-0009: Weak or no authentication
- HoT-TAI-0013: Account lockout
- HoT-TAI-0014: Privilege Escalation
- HoT-TAI-0019: Insecure password recovery mechanism
 Update Mechanism
Update Mechanism
- HoT-TAI-0007: Weak access controls
- HoT-TAI-0011: Firmware and application updates sent without encryption
- HoT-TAI-0021: Update authentication & Update Integrity verification / Updates not signed
- XHoT-TAI-0042: Missing update mechanism
- XHoT-TAI-0043: No manual update mechanism
 Vendor Backend APIs
Vendor Backend APIs
- HoT-TAI-0002: Injection
- HoT-TAI-0007: Weak access controls
- HoT-TAI-0008: Weak or no transport encryption
- HoT-TAI-0009: Weak or no authentication
 3rd Party Backend APIs
3rd Party Backend APIs
- HoT-TAI-0008: Weak or no transport encryption
- HoT-TAI-0009: Weak or no authentication
 Ecosystem (General)
Ecosystem (General)
- HoT-TAI-0008: Weak or no transport encryption
- HoT-TAI-0009: Weak or no authentication
- HoT-TAI-0032: Insecure password recovery mechanism
- HoT-TAI-0034: Lack of enrollment security
 Cloud Web Interface
Cloud Web Interface
- HoT-TAI-0001: Password / Credential Management
- HoT-TAI-0002: Injection
- HoT-TAI-0008: Weak or no transport encryption
- HoT-TAI-0009: Weak or no authentication
- HoT-TAI-0012: Insecure direct object references
- HoT-TAI-0013: Account lockout
- HoT-TAI-0014: Privilege Escalation
- HoT-TAI-0015: Replay attack
- HoT-TAI-0019: Insecure password recovery mechanism
- HoT-TAI-0022: Logging Options
 Psychosocial
Psychosocial
- HoT-TAI-XXXX: TBD
 User Awareness
User Awareness
- HoT-TAI-XXXX: TBD